If you follow this blog, you may have noticed that I am extremely passionate about Software Defined Perimeters (SDP). As someone who pioneered the first open source reference architecture and specifications of SDP for the Cloud Security Alliance (CSA), I’ve seen the evolution of SDP — from a DISA concept to a game-changing security architecture, particularly as it relates to its new role in enabling an effective Zero Trust model.
I follow everything being written about SDPs and I am concerned about continued misunderstanding of the dynamics of an SDP architecture. Some vendor solutions focus on one component of SDP, enabling them to build on an inherent strength from their legacy network-based offerings. SDP is not a network centric solution. The CSA open source calls for inclusion of two features – a gateway and a controller.
At Waverley Labs, during multiple implementations, we discovered that an enhanced gateway provides significant benefits. While a controller is critical to the architecture it is the gateway that increases resilience of the SDP focused on applications – as an overlay to the existing network infrastructure.
Recently I’ve been enjoying TechTarget’s increasing coverage of SDP when a recent article caught my attention, “Understanding the zero trust-SDP relationship”. The writer explains from his perspective how an SDP embodies the principles of zero trust at the network level.
In reality, SDP is a fundamentally application-centric approach that is central to a true zero trust strategy – particularly for complex cloud native applications or applications refactored for the cloud.
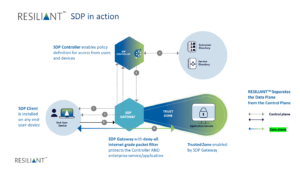
A fundamental problem with the article is that it makes the case that the Controller is the most important component of SDP architecture. While the Controller is defined to enable policy decisions, the article neglects to mention the importance and need to automate dynamic enforcement of policy decisions which is performed by the Gateway. Following the NIST guidance you need to separate the control plain from the data plain – policy decision from policy enforcement. One without the other puts the value of SDP at risk.
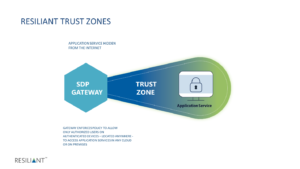
The value of SDP in a Zero Trust model must be its ability to make applications and services invisible and second, its ability to deny all access to users without credentials – a cyber passport of sorts – authorizing access to applications and services in the cloud. To do this, SDPs include a Gateway that provides dynamic enforcement of policy – casting what we call a Trust Zone — for the applications it is protecting.
Waverley Labs developed its SDP, architected to CSA specifications, that has been effectively deployed in government organizations for more than five years. Next month, Waverley Labs will launch the commercial offering of its SDP under the label of RESILIANT.
Most SDP solutions, based on the Cloud Security Alliance open source specification, include a gateway. But, not all Gateways provide automated enforcement of policy decisions. The RESILIANT SDP separates the control plan from the data plane and introduces a new, powerful dynamic GATEWAY. By this we mean separating the controls of the requesting host (i.e. users and their devices) from the requirements of the accepting host (i.e. the application or services). When evaluating SDP offers, ensure that the SDP performs granular inspection of credentials to enforce policy and dynamically deny unauthorized users and/or unauthenticated devices.
Is the SDP Gateway application service specific and can it perform at internet scale? RESILIANT SDP features a service specific gateway – an internet scale, deny all packet filter – which dynamically enforces policies controlling which users on validated devices are authorized to access a specific service – located anywhere.
The RESILIANT SDP, includes a Controller – the policy decision point – to authenticate and authorize users and their devices. The Gateway dynamically enforces the policy and admits only credentialed users.
The Gateway casts a Trust Zone, protecting services, making them invisible and leaving attackers and unauthorized users abandoned outside the Gateway. The RESILIANT Trust ZoneTM is unique and is becoming the gold standard by which, the effectiveness of SDPs should be evaluated and judged.
Think of the Trust Zone this way. If someone is using a device authenticated by the controller, but they are not an approved user of the target service, they will be denied access.
Even if a bad actor has stolen credentials (making them an approved user), they will still be denied access since they are on a device not authenticated by the controller.
Government organizations using the Waverley SDP, formerly known as Panther, have effectively reduced the number of successful attacks and trust the gateway to admit only credentialed users using validated devices into the trust zone even while attacks are ongoing. Based on this success Waverley made the decision to launch RESILIANT SDP.
For more info, visit the newly launched RESILIANT SDP website. For more background on the evolution of RESILIANT read this white paper featuring Waverley Lab’s first deployment of SDP. Titled Software Defined Perimeter (SDP) and Zero Trust the paper evaluates the use of SDP and illustrates how a Zero Trust implementation featuring the Waverley SDP enables organizations to defend new variations of old attack methods that are constantly surfacing in perimeter-centric networking models.
Let me know what you think. Leave me a comment or reach out to me via LinkedIn to connect and have a discussion.
###